
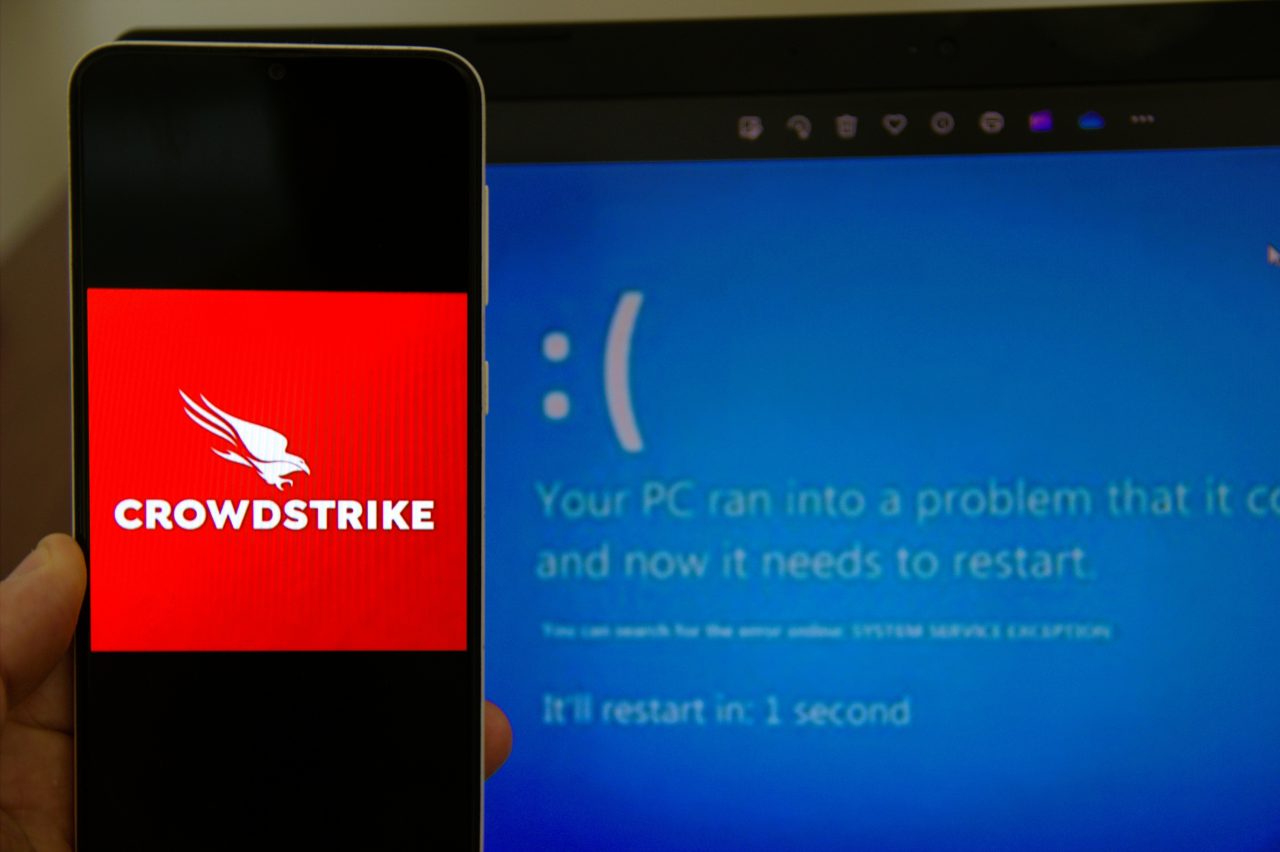
The recent incident involving CrowdStrike’s faulty software update underscored the critical importance of maintaining rigorous standards in cyber security. As this event disrupted millions of businesses worldwide, from airlines to healthcare providers, it became evident that a single point of failure can cascade into widespread chaos. The disruption caused by the misconfigured Falcon sensor on the Windows operating system, leading to widespread system crashes, highlighted the need for thorough testing and validation processes for all software updates. Businesses must now place greater emphasis on not only fortifying their own cyber security measures but also meticulously evaluating their service providers and partners. The cyber security firm must ensure that their support portal provides immediate assistance and access to recovery keys to mitigate such issues. Additionally, this event has accelerated the urgency for implementing robust contingency plans to ensure operational resilience amidst unforeseen system failures. By learning from the extensive operational disruptions and financial repercussions experienced during this crisis, including issues with the channel file, businesses can better prepare to protect themselves against future cyber threats.
The CrowdStrike cyber event, involving the American cyber security firm, severely impacted a multitude of industries, notably airlines, healthcare, media and broadcasting, financial services, retail, and emergency services. These sectors faced significant operational disruptions, from blue screen system crashes to service interruptions and delays in emergency response times. To mitigate future risks, it is essential for these industries to adopt comprehensive cyber security strategies, including the utilisation of CrowdStrike Falcon. This includes rigorous testing and validation of software updates, developing and maintaining robust contingency plans to ensure business continuity, and conducting regular risk assessments. Moreover, partnering with reliable and transparent cyber security providers and fostering a resilient cyber security culture within the organisation are pivotal steps to safeguarding against similar incidents in the future. Utilising recovery keys and ensuring continuous updates are critical measures. The attack on DNC servers serves as a stark reminder of the importance of these proactive measures. By implementing these strategies, businesses can enhance their resilience against potential cyber threats and maintain operational stability.
Rigorous testing and validation processes are paramount in the realm of software updates, as demonstrated by the recent CrowdStrike incident. When CrowdStrike released a faulty Falcon Sensor configuration update, it led to mass system crashes and operational disruptions across various industries. This highlighted the devastating effects that a single flawed update can have. Comprehensive testing ensures that any potential issues are identified and rectified before deployment, thereby preventing widespread chaos and financial losses. Validation processes serve as an additional safety net, ensuring that updates meet the required standards and function correctly within the operational environment. CrowdStrike support was inundated with recovery key requests and troubleshooting for the spinner white decorative issues faced by users. George Kurtz, CEO of CrowdStrike, emphasised the importance of these practices to avoid the pitfalls of untested updates, maintain operational continuity, and safeguard systems against unforeseen failures. The lessons learned from CrowdStrike’s misstep underscore the critical need for meticulous testing and validation in safeguarding digital infrastructure.
In the face of cyber threats and unforeseen system failures, the necessity of robust contingency plans cannot be overstated. The CrowdStrike Falcon Platform incident serves as a poignant reminder of how a single point of software failure in an operating system can cascade into widespread operational and financial disruptions. Contingency plans are not just a luxury but a crucial element in ensuring business resilience. They encompass predefined actions and protocols designed to maintain or quickly restore business operations when digital infrastructure, including cloud and data services, is compromised. By identifying critical processes and establishing clear lines of communication and responsibility, companies can navigate through crises with reduced downtime and impact. Furthermore, regularly updating and rehearsing these plans ensures that employees are well-prepared to act efficiently in an emergency. In a landscape where cyber threats like malware are ever-evolving, having a well-structured contingency plan is indispensable for sustaining operational continuity and protecting organisational integrity. Keeping devices secure with the latest updates is also essential in maintaining the trust of customers and safeguarding the company’s digital assets.
The CrowdStrike incident has starkly exposed the vulnerabilities that a single point of failure can create within business operations. When the cyber security firm’s misconfigured sensor update led to mass system crashes, it disrupted services across various critical sectors, including airlines and healthcare. CEO George Kurtz emphasised that the problem began with a channel file error. This incident underscores the interconnected nature of modern digital infrastructures and the cascading effects that can ensue from a single malfunction. It highlights the necessity for companies to not only ensure the reliability of their own systems but also to scrutinise the stability and reliability of their service providers. With many devices and computers affected, including those running Microsoft software, the incident led to numerous online requests for help. The report indicated that the misconfigured update was installed and deployed without rigorous testing. This vulnerability emphasises the importance of diversifying security strategies and incorporating multiple layers of checks and balances to safeguard against such points of failure. By adopting a comprehensive approach that includes rigorous testing, validation processes, and proactive contingency planning, businesses can better protect themselves against disruptions and maintain operational resilience in an increasingly digital world.
The CrowdStrike incident has highlighted the critical need for companies to diligently scrutinise their service providers and partners as an integral aspect of their security measures. In an interconnected digital ecosystem, the reliability of third-party vendors can significantly influence a company’s overall security posture. Therefore, businesses must rigorously evaluate the cyber security practices of their service providers, ensuring they adhere to robust security protocols and have contingency plans for system failures. Regular audits, compliance checks, and transparent communication channels with these partners can help identify potential vulnerabilities before they become major issues. By taking these proactive steps, companies not only safeguard themselves against indirect threats but also reinforce a culture of shared responsibility and resilience within their broader operational network. This includes ensuring that cloud services, devices, and computers used by both the company and its customers are secure. Maintaining operational stability and protecting critical assets in an increasingly complex cyber landscape is essential, and strong connections with reliable vendors are key to this process.
In the wake of the CrowdStrike incident, there has been a noticeable uptick in phishing scams targeting businesses, exploiting the heightened sense of urgency and uncertainty. Cybercriminals are leveraging sophisticated tactics, including impersonating trusted entities and crafting convincing messages that exploit the fear of security breaches. To protect your business and customers against these malicious campaigns, it is essential to implement comprehensive security measures. Start by educating employees on recognising phishing attempts and the importance of scrutinising unexpected messages. Employ robust email filtering solutions to detect and block malicious emails before they reach any device. Additionally, enforcing multi-factor authentication (MFA) can add an extra layer of security, ensuring that compromised credentials alone are insufficient for gaining access to your systems. Regularly updating and patching software can close vulnerabilities, making it harder for attackers to infiltrate your network. By adopting these proactive measures, businesses can bolster their defences against phishing scams and safeguard their digital assets and customers.
In the rapidly evolving digital landscape, maintaining up-to-date security protocols is paramount to safeguarding your business. The CrowdStrike incident has demonstrated that even a minor lapse in security can have extensive repercussions across multiple sectors. To protect against such vulnerabilities, businesses must connect with the latest updates and patches to their systems, closing any security gaps that cybercriminals might exploit. Ensuring that all software, from operating systems to applications, is involved in applying the latest security patches can effectively mitigate the risk of attacks. Additionally, adopting intelligent security measures such as multi-factor authentication (MFA), robust encryption, and continuous monitoring of networks can further enhance an organisation’s defence mechanisms. By proactively managing security protocols and staying ahead of potential threats, businesses can maintain operational integrity, reduce downtime, and foster a secure digital environment that supports their long-term growth and resilience.
As the digital landscape continues to evolve, the complexities of cyber security grow increasingly challenging for businesses. Outsourcing cyber security functions can provide a pragmatic solution to stay ahead of potential threats. By enlisting the expertise of specialised firms, businesses can benefit from cutting-edge technologies and strategies that may be beyond their in-house capabilities. Such firms are adept at managing the latest security risks, offering a spectrum of services from real-time threat monitoring to advanced threat intelligence. Outsourcing also allows internal IT teams to focus on core business functions, enhancing overall productivity and efficiency. Moreover, partners in cyber security often have stringent compliance and audit practices, which can help businesses adhere to regulatory requirements and mitigate risks associated with cyber threats. In essence, outsourcing cyber security can fortify a company’s defence mechanisms, offering peace of mind and operational resilience in a continually shifting digital terrain.

This website uses cookies to improve your experience. Choose what you're happy with.
Required for the site to function and can't be switched off.
Help us improve the website. Turn on if you agree.
Used for ads and personalisation. Turn on if you agree.
This website uses cookies to improve your experience. Choose what you're happy with.
Required for the site to function and can't be switched off.
Help us improve the website. Turn on if you agree.
Used for ads and personalisation. Turn on if you agree.